Computer Network Topology
 Topology describes the structure of a network or how a network is designed. This pattern is very closely related to media access and delivery methods used. There were highly dependent topology with geofrapis location of each terminal, the quality control needed in the communication or messaging, as well as the speed of data transmission. In the definition of topology is divided into two, namely the physical topology (physical topology), which indicates the position of the physical cabling and topology of logic (logical topology) which shows how a medium accessible by the host.
The physical topology is commonly used in building a network is:
Point to Point (Point to Point).
Networking ketitik point is the most simple networks but can be used widely. Once the simplicity of this network, which is often not considered as a network but only an ordinary communication. In this case, both nodes have the same level position, so that any node can initiate and control the relationship in the network. Data sent from one node another conclusion as the recipient directly, such as between terminals with the CPU.
Star Network (Star Network).
In a star configuration, some existing equipment will be linked into a central computer. Existing controls will
Topology describes the structure of a network or how a network is designed. This pattern is very closely related to media access and delivery methods used. There were highly dependent topology with geofrapis location of each terminal, the quality control needed in the communication or messaging, as well as the speed of data transmission. In the definition of topology is divided into two, namely the physical topology (physical topology), which indicates the position of the physical cabling and topology of logic (logical topology) which shows how a medium accessible by the host.
The physical topology is commonly used in building a network is:
Point to Point (Point to Point).
Networking ketitik point is the most simple networks but can be used widely. Once the simplicity of this network, which is often not considered as a network but only an ordinary communication. In this case, both nodes have the same level position, so that any node can initiate and control the relationship in the network. Data sent from one node another conclusion as the recipient directly, such as between terminals with the CPU.
Star Network (Star Network).
In a star configuration, some existing equipment will be linked into a central computer. Existing controls will  be concentrated at one point, such as workload and set the settings of existing resources. All links should be related to the central data channel if you want to target other conclusion. In this case, when the center was down, then all terminals may also be disrupted. Star network model is relatively very simple, so widely used by the parties of the bank which usually have many branches in different locations. With the existence of this star configuration, then there are all sorts of activities at the branch offices it can be properly controlled and coordinated. In addition, the education world too much advantage of this star networks to control their students' activities.
Excess
· Damage on one channel only affect the channel network and the station adrift.
· Security level is high.
· Hold on a busy network traffic.
· Additions and reductions station can be done easily.
Shortage
· If the node was malfunctioning, then the entire network to a halt.
Handling
· Prepared Need backup middle node.
Ring Networks (Ring Network)
In this network there are several devices are connected to one another and ultimately form the chart as well as a ring
be concentrated at one point, such as workload and set the settings of existing resources. All links should be related to the central data channel if you want to target other conclusion. In this case, when the center was down, then all terminals may also be disrupted. Star network model is relatively very simple, so widely used by the parties of the bank which usually have many branches in different locations. With the existence of this star configuration, then there are all sorts of activities at the branch offices it can be properly controlled and coordinated. In addition, the education world too much advantage of this star networks to control their students' activities.
Excess
· Damage on one channel only affect the channel network and the station adrift.
· Security level is high.
· Hold on a busy network traffic.
· Additions and reductions station can be done easily.
Shortage
· If the node was malfunctioning, then the entire network to a halt.
Handling
· Prepared Need backup middle node.
Ring Networks (Ring Network)
In this network there are several devices are connected to one another and ultimately form the chart as well as a ring . Ring network does not have a point that acts as a central regulator or the data traffic, all nodes have the same level. Data sent will go throu
Figure 3.1 star network topologygh several nodes, so arrive at the destination node. In the present data, the network can move in one or two directions. However, existing data remain moving in one direction at a time. First, existing messages will be delivered from other ketitik point in one direction. When encountered a failure, for example, there is damage to the existing equipment, so existing data will be sent with the second, then the message is transmitted in the opposite direction, and could ultimately end up at destination. Such a configuration is relatively more expensive when compared with the star network configuration. This is due, any existing node will act as a computer that will handle every application that it faces, and should be able to share resources on the existing network. In addition, this system is more suitable to use for systems that are not centralized (decentralized-system), which is not required to do a particular priority.
Figure 8.2 Network topology ring
Tree Network (Network Tree)
In tree networks, there are several levels of nodes (node). Central or higher level node, another node can set a lower level. Data sent to the central node first. For example to move from a computer with a node-3 node kekomputer-7 as well as in the figure, the data must pass through node-3, 5 and node-6 before ending at the node-7. Keungguluan network tree model like this is, can the establishment of a group that is required at all times. For example, companies can form a group consisting of terminal accounts, as well as on other groups formed to terminal sales. The weakness is, if the node is higher then does not work, then the other group who are below it eventually also became ineffective. How the
. Ring network does not have a point that acts as a central regulator or the data traffic, all nodes have the same level. Data sent will go throu
Figure 3.1 star network topologygh several nodes, so arrive at the destination node. In the present data, the network can move in one or two directions. However, existing data remain moving in one direction at a time. First, existing messages will be delivered from other ketitik point in one direction. When encountered a failure, for example, there is damage to the existing equipment, so existing data will be sent with the second, then the message is transmitted in the opposite direction, and could ultimately end up at destination. Such a configuration is relatively more expensive when compared with the star network configuration. This is due, any existing node will act as a computer that will handle every application that it faces, and should be able to share resources on the existing network. In addition, this system is more suitable to use for systems that are not centralized (decentralized-system), which is not required to do a particular priority.
Figure 8.2 Network topology ring
Tree Network (Network Tree)
In tree networks, there are several levels of nodes (node). Central or higher level node, another node can set a lower level. Data sent to the central node first. For example to move from a computer with a node-3 node kekomputer-7 as well as in the figure, the data must pass through node-3, 5 and node-6 before ending at the node-7. Keungguluan network tree model like this is, can the establishment of a group that is required at all times. For example, companies can form a group consisting of terminal accounts, as well as on other groups formed to terminal sales. The weakness is, if the node is higher then does not work, then the other group who are below it eventually also became ineffective. How the network is relatively slow tree
Figure 8.3 Network topology tree
Bus Network
Another configuration is known as a bus-network, suitable for areas that are not too large. Each computer (each node) will be connected by a communication cable through an interface. Each computer can communicate directly with computers or other equipment contained within the network, in other words, all nodes have the same position. In this case, the network is not dependent on the existing computer center, so that when one device or one node is destroyed, the system can still operate. Each node has an existing address or nature itself. So that access to the data from one node, the user or the user simply mentioning the address of the node in question. Buses are the development of excellence network topology or adding new workstations can be done easily without disturbing other workstations. The weakness of this topology is that if there is interference along the center of the entire cable network would be disrupted.
Figure 8.4 Network topology bus
Plex Network (Network Combination)
Network is a truly interactive, where every node has the ability to directly access not only to computers but also with other devices or nodes. In general, the network has a shape similar to a star network. Organization of existing data using the de-centralization, is to perform maintenance, use centralized facility.
Figure 8.5 Network topology combinations
Topology and logic are generally divided form the two types, namely:
a. Broadcast Topology
In simple terms can be described that is a host that sends data to all other hosts on the network media.
b. Token Passing Topologies
Set the data transmission to the host through the media by using the token that regularly rotates in a whole host. The host can only send data only if that host has a token. By this token, collision can be prevented.
Factors - factors that need consideration for the selection of topology is as follows:
· Course fee
What is the most efficient system is needed within the organization.
· Speed
To what extent has the needed speed in the system.
· Environment
Such as electricity or factors - other environmental factors, influencing the type of hardware used.
· Size
Up to how big the size of the network. Does the network need a file server or a dedicated server.
· Connectivity
Does the other user who uses a laptop computer to access the network from various locations.
network is relatively slow tree
Figure 8.3 Network topology tree
Bus Network
Another configuration is known as a bus-network, suitable for areas that are not too large. Each computer (each node) will be connected by a communication cable through an interface. Each computer can communicate directly with computers or other equipment contained within the network, in other words, all nodes have the same position. In this case, the network is not dependent on the existing computer center, so that when one device or one node is destroyed, the system can still operate. Each node has an existing address or nature itself. So that access to the data from one node, the user or the user simply mentioning the address of the node in question. Buses are the development of excellence network topology or adding new workstations can be done easily without disturbing other workstations. The weakness of this topology is that if there is interference along the center of the entire cable network would be disrupted.
Figure 8.4 Network topology bus
Plex Network (Network Combination)
Network is a truly interactive, where every node has the ability to directly access not only to computers but also with other devices or nodes. In general, the network has a shape similar to a star network. Organization of existing data using the de-centralization, is to perform maintenance, use centralized facility.
Figure 8.5 Network topology combinations
Topology and logic are generally divided form the two types, namely:
a. Broadcast Topology
In simple terms can be described that is a host that sends data to all other hosts on the network media.
b. Token Passing Topologies
Set the data transmission to the host through the media by using the token that regularly rotates in a whole host. The host can only send data only if that host has a token. By this token, collision can be prevented.
Factors - factors that need consideration for the selection of topology is as follows:
· Course fee
What is the most efficient system is needed within the organization.
· Speed
To what extent has the needed speed in the system.
· Environment
Such as electricity or factors - other environmental factors, influencing the type of hardware used.
· Size
Up to how big the size of the network. Does the network need a file server or a dedicated server.
· Connectivity
Does the other user who uses a laptop computer to access the network from various locations.
Don't Stop to Defrag your windows..How??
Windows Defrag Disk Defragmenter is one inherent feature of Windows that is used to analyze the volume of the drive and rearrange all the files and folders that exist on the drive that the defrag. The goal is that all files and folders are tidied his composition so that the system can be easier and faster when accessing files and folders. In other words, if you defrag the drive / volume so our computer will be faster. How to defrag windows pake: 1. Close all applications, so that maximum results defrag process. 2. Start menu -> Programs -> Accessories -> System Tools -> Disk Defragmenter 3. Then the drive volume will appear to list 4. Select the volume that would at Defrag 5. Analyze to analyze only 6. Defragment to analyze and then after finishing the analysis will proceed to defrag the volume of the selected process. But if going to defrag should confirm when the process goes not to stop by any factor (eg power failure, restart, etc.). Because if the defrag process is not finished yet suddenly stopped, it could be your hard drive is going bad sectors or broken.
Microprocessors and microcomputers
1.Mikroprosesor Microprocessors are single chip that has a series of arithmetic, logic and control (Arithmetic Logic Unit / ALU and Control Unit / CU), from a general-purpose processing, control systems and counting systems. Thus the combination sometimes include a number of reminders (memory) in flakes (chips) are equal, ie central processing units (central processing unit) of the system, that called prosesor.serpih CPU can be obtained from various manufacturers in a variety of long words: 4,8,12,16,32 or 64bit. The technology in use adalalah * CCD, PMOS, NMOS, CMOS, Bipolar, IIL, DMOS, VMOS table 2. CENTRAL PROCESSING UNIT (CPU) CPU is the processing instructions program.pada microcomputer, the processor is called a microprocessor. CPU consists of two main sections, namely control unit (control unit) and the arithmetic and logic unit (arithmetic and logic unit). In addition there are also some deviation of the size kecilyang called registers. 2 3. CONTROL UNIT The task is a control unit: 1. regulate and control the means of input and output 2. Set instructions from main memory. 3. Mengmbil data from main memory if needed down the process. 4. Sending Instructions to ALU arithmetic calculations or if there is comparison logic, and supervises the work of the ALU. 5. Storing the results of the process into main memory. 4.ARITHMETIC AND LOGIC UNIT (ALU) * The main task of the ALU is to perform all arithmetic calculations or mathematics that occurs in accordance with the instructions of the program. * In addition, the decision of the ALU also perform logic operations in accordance with program instructions. 5. REGISTER Register is a small savings which have high speed, much faster about 5 to 10 times in comparison with the speed of return data from the recorder or play memory.Register in use to store instructions and data that are in the process olrh CPU, medium of instructions and other data who were waiting for the process is still in store in main memory. 6. Array PROCESSOR When a large number of calculations to be done, to speed up processing time, can be used in an array processor. An array processor or Coprocessor is a separate processor that can be added to the main processor. With an array processor, the computation of a large and difficult arithmatika can be done by breaking aiau dividing the computation and carried out jointly between central processor and array processor. Because the main function of the co-processor or processor array is a complex mathematical calculation, it is also called math-processor or numeric data processor. 7. Microprocessors and microcomputers TURNING INTO To build all the necessary tasks a computer, the CPU must be equipped with reminders (memory) additional hour (clock), the mobile intermediate adapter (PIA) for the instrument input and output (I / O). 4 The number of flakes Chip) complementary around the microprocessor in the picture above ranged from 10 to 80 pieces, and mounted on a printed circuit board (printed circuit board / PCB). The number of transistors on board equivalent to more than 100,000, even up to tens of millions of 5 8. MAIN MEMORY CPU only can store data and instructions in a register of its small size, so can not store all the information needed for the entire process from the program. To overcome this, then the processing device is equipped with a capacity greater savings, that is played is also called primary storage or storage. Main memory consists of RAM and ROM a. ROM ROM: read only, not to fill something into the ROM. The contents of ROM is already filled by the manufacturer, a system OPERATING! (Operating System) which consists of basic courses required by the computer system, such as a program to regulate the appearance of characters on the screen, filling the key button on the keyboard fatherly certain control purposes and the bootstrap program. Bootstrap program is needed in the first time a computer system is activated - boot (cold boot / warm boot) instructions stored in ROM or microinstructions called microcode. Also referred to as firmware, as hardware and software put together by the manufacturer. b. RAM RAM: all data and programs that are inserted through the instrument input, are stored in main memory used knususnya in RAM (Random Access Memory). RAM is memory that can be accessed (optional / retrieved its contents) by the programmer. RAM structure is divided into four parts: 1. Added storage - accommodates input is entered via input devices. 2. -Storage program stores all the program instructions to be processed. 3. Working storage-storing data to be processed and the results of processing 4. Accommodate the output storage-final results from the processing of data to be displayed to the output device. Input is entered through the input device, was first housed in the input storage beforehand, when the input shaped the program, then transferred to the program and if the form of data storage, will be transferred to working storage. Results of processing are also accommodated in the working storage and the results will be displayed to the output device was transferred to the output storage. 9. CACHE MEMORY Multiple CPU using a cache memory or buffer memory with the intention of the CPU to work more efficiently and reduce the time wasted. Without cache memory, the CPU will wait until the data or instructions received from main menrory or waiting for the results of the processing is completed is sent to main memory, the new process can then be performed. Padanal process of main memory is slower than the speed of the register. Cache memory is placed in between the CPU and main memory. Cache memory should be faster than main memory and has a large enough size, but not as much main memory. Actually the cache memory is not necessary when main memory as fast as cache memory, but the way it is not economical.
Take Care your Self when Browsing...
How to Be Safe on Social Networking Sites.
its normal question from people who are always stay browsing on internet, and now, I write this article to help all people who need information to be safe on social networking sites likes Facebook, Twitter, and other.here we goes.Would you tell a complete stranger all about your family, work, love life, hobbies and interests? And give them some personal photos to look at too? Most people approached on the street would probably answer ‘no’ to the above questions. But on the Internet, that’s exactly what millions of us are doing on the hugely popular social networking sites and chat rooms. Online social networks are fun and hip, but they also present a major security concern for Internet users.
Today your online wellbeing has a direct impact on the rest of your life. So enjoy the social networking sites while also keeping security in mind. That way you are protecting your computer, money and reputation, as well as your family and friends.
Steps
- Don’t reveal too much: Each web site provides different levels of privacy settings to control access to your profile page and your interaction with others. Identity theft is a major industry on the Internet and information extracted from social networking sites is used by criminals to spam e-mails and for targeted attacks on specific individuals and companies, using sophisticated social engineering techniques.
- Beware of spam messages: It could be an e-mail pretending to be from someone you know, addressing you by your first name and mentioning the names of your children. It doesn’t look like a spam message and it can trick you into revealing even more sensitive information. Similar methods are also used to gain financial information from businesses.
- Educate yourself: As social networking sites and chat rooms are especially attractive to children and teenagers, it is essential that parents educate them about safe online behavior and keep tabs on what they are doing online.
- Maintain a good reputation: It’s worth remembering that whatever you post on your profile page, or other community forum, remains in the public sphere long after you log out of the web site. This includes the crazy stuff and wild photos that you posted on Facebook but decided to delete ten minutes later because it suddenly seemed like a bad idea. The problem is that you can’t really retract it. Once it’s out there on the Web, you have little control over who copies the material, where it is used and how widely it gets distributed.
Tips
- Bebo provides an excellent summary of the security issues involving social networking sites for both parents and children at www.bebo.com/Safety.jsp Another recommended site for parents is www.saferinternet.org.
- The best way to guard against such threats is to install software like F-Secure Internet Security 2009, which updates your computer’s defenses automatically and makes sure you won’t be the one spreading worms among your network of friends. It’s also important to update your web browser, so remember to click on the security updates for Internet Explorer and Mozilla Firefox, or any other browser you are using. This helps to keep your computer patched up against the viruses.
edit Warnings
- Social networking sites are also used by predators and pedophiles searching for possible victims. It’s easy for anyone to adopt false identities on the Web, so you should maintain a healthy skepticism over what you see and hear on social networking sites. The bright young student you are conversing with could always be a middle-aged fraud. If you want to meet a person who you have befriended online, always do it in a public place, preferably accompanied by someone.
- Many online social networks encourage users to import content like video clips and also accept third party add-on applications. This can be exploited by virus writers as a way of getting malicious code into the networks, such as the worm which spread rapidly on Orkut’s web site last year, infecting an estimated 655,000 users in Brazil.
10 Most Expensive Collectibles in the World
Perhaps we never purchase any item to be collected. Whether it's art items like paintings, or knick-knacks with a particular character, or flowers and plants. Sometimes to get it must be hard.
Maybe these things have meaning for us or maybe just for investment. Well, talk collectible items, about what kind of goods that were collected by the rich world and how much money they must spend in order to have them.
1. 1961 Ferrari California  Spyder Prices Break Record with U.S. $ 10.9 Million Dollars Dollars (110 billion)
Cool antique sports car was purchased and the price is amazing at auction in Maranello, Italy last year by Chris Evans, a famous British radio host. Ferrari, which was previously owned by actor James Coburn, eventually sold for 10.9 million dollars (110 billion), almost double than expected.
2. World's Most Expensive Number Plate Worth U.S. $ 14.3 Million Dollars (150 Billion)
Spyder Prices Break Record with U.S. $ 10.9 Million Dollars Dollars (110 billion)
Cool antique sports car was purchased and the price is amazing at auction in Maranello, Italy last year by Chris Evans, a famous British radio host. Ferrari, which was previously owned by actor James Coburn, eventually sold for 10.9 million dollars (110 billion), almost double than expected.
2. World's Most Expensive Number Plate Worth U.S. $ 14.3 Million Dollars (150 Billion)
 Rich people are usually willing to pay more to buy a special numbered license plates for his car. But the license plate on this one worth U.S. $ 14.3 million dollars (150 billion!), United Arab Emirates businessmen purchased, Saeed Abdul Ghafour.
This plate does show itself is the number one because this number plate was labeled with only the figure "1". This number plate auction held at the 7 star hotel Emirates Palace Hotel in Abu Dhabi. Imagine if the license plate was placed in a Ferrari on top and a combination of expensive cars with expensive license plate as well. Wow!
3. Rare Blue Diamond Sold the World Record Price of U.S. $
Rich people are usually willing to pay more to buy a special numbered license plates for his car. But the license plate on this one worth U.S. $ 14.3 million dollars (150 billion!), United Arab Emirates businessmen purchased, Saeed Abdul Ghafour.
This plate does show itself is the number one because this number plate was labeled with only the figure "1". This number plate auction held at the 7 star hotel Emirates Palace Hotel in Abu Dhabi. Imagine if the license plate was placed in a Ferrari on top and a combination of expensive cars with expensive license plate as well. Wow!
3. Rare Blue Diamond Sold the World Record Price of U.S. $ 8.9 Million Dollars (90 Billion)
Blue diamonds weighing 13.9 carats of diamonds is to make a record turnover after sold at a price of U.S. $ 8.9 million dollars (90 billion) at auction house Christie's in Geneva last year. This diamond was mentioned very rare and contains boron, making it a bluish color.
4. Honus W
8.9 Million Dollars (90 Billion)
Blue diamonds weighing 13.9 carats of diamonds is to make a record turnover after sold at a price of U.S. $ 8.9 million dollars (90 billion) at auction house Christie's in Geneva last year. This diamond was mentioned very rare and contains boron, making it a bluish color.
4. Honus W agner Baseball Card Sold in 1909 to U.S. $ 1.62 Million Dollars (17 Billion)
Maybe you think this world's most expensive baseball card. In fact no, there is much more expensive, the other Wagner baseball card was sold for U.S. 2.8 million dollars (29 billion) in 2007. Wagner Looks like this is a great baseball player in his time. God knows how old their income in the year 1909.
5. 3 Mon Rare stamps sold for more than U.S. $ 1 Million Dollars (10 Billion)
3-cent stamps "B Grill" like a rose-color
agner Baseball Card Sold in 1909 to U.S. $ 1.62 Million Dollars (17 Billion)
Maybe you think this world's most expensive baseball card. In fact no, there is much more expensive, the other Wagner baseball card was sold for U.S. 2.8 million dollars (29 billion) in 2007. Wagner Looks like this is a great baseball player in his time. God knows how old their income in the year 1909.
5. 3 Mon Rare stamps sold for more than U.S. $ 1 Million Dollars (10 Billion)
3-cent stamps "B Grill" like a rose-color ed This is one of four stamps that remain similar. An unknown buyer won lelangnya costing U.S. $ 1.035 million dollars (10 billion). Looks like a cool collection of stamps you are not worth anything compared to this one. Hmmm ...
6. Russian Rich Buying Houses villa in the Riviera Worth U.S. $ 750 Million Dollars (7.5 Trillion)
ed This is one of four stamps that remain similar. An unknown buyer won lelangnya costing U.S. $ 1.035 million dollars (10 billion). Looks like a cool collection of stamps you are not worth anything compared to this one. Hmmm ...
6. Russian Rich Buying Houses villa in the Riviera Worth U.S. $ 750 Million Dollars (7.5 Trillion)
 The building, built by King Leopold II of Belgium in 1902, purchased in 2008 at a price far above the actual prices, even far more expensive than the most luxurious modern villa there. Mikail Prokhorov mention paying more than U.S. $ 750 million dollars (7.5 trillion) to buy the Villa Leopolda located between Nice and Monaco this.
7. Francis Bacon's paintings record sales of U.S. $ 86 Million Dollars (870 Billion)
1974-77 triptych by Fra
The building, built by King Leopold II of Belgium in 1902, purchased in 2008 at a price far above the actual prices, even far more expensive than the most luxurious modern villa there. Mikail Prokhorov mention paying more than U.S. $ 750 million dollars (7.5 trillion) to buy the Villa Leopolda located between Nice and Monaco this.
7. Francis Bacon's paintings record sales of U.S. $ 86 Million Dollars (870 Billion)
1974-77 triptych by Fra ncis Bacon (1909-1992) sold for U.S. $ 86.3 million dollars (870 billion) in May last year making it the most expensive artwork ever sold at an auction and the most valuable contemporary work ever sold in Europe.
If you wonder how the price could soar as high as that, just imagine there are people who have so much money just for their collections budget, which seemed of larger amount of money owned by many small countries.
8. 2.1 Million U.S. Dollars (21 Billion) For squillionaires Dinner with Warren Buffett
In the most expensiv
ncis Bacon (1909-1992) sold for U.S. $ 86.3 million dollars (870 billion) in May last year making it the most expensive artwork ever sold at an auction and the most valuable contemporary work ever sold in Europe.
If you wonder how the price could soar as high as that, just imagine there are people who have so much money just for their collections budget, which seemed of larger amount of money owned by many small countries.
8. 2.1 Million U.S. Dollars (21 Billion) For squillionaires Dinner with Warren Buffett
In the most expensiv e charity auction on eBay, an investment manager from China won the opportunity to have dinner with Warren Buffett squillionaires costing U.S. $ 2.1 million dollars (21 billion).
Zhao Danyang of the Pureheart China Growth Investment Fund, Hong Kong seems to have the same philosophy which he thought Buffett, one of them looking for companies with competitive advantages that are sold cheaper than the real condition. I hope dinner produce something that fits with what she paid.
9. The World's Most Expensive Hours Worth of U.S. $ 6.5 Million Dollars (65 Billion)
e charity auction on eBay, an investment manager from China won the opportunity to have dinner with Warren Buffett squillionaires costing U.S. $ 2.1 million dollars (21 billion).
Zhao Danyang of the Pureheart China Growth Investment Fund, Hong Kong seems to have the same philosophy which he thought Buffett, one of them looking for companies with competitive advantages that are sold cheaper than the real condition. I hope dinner produce something that fits with what she paid.
9. The World's Most Expensive Hours Worth of U.S. $ 6.5 Million Dollars (65 Billion)
 Watches costing U.S. $ 6.5 million dollars (65 billion) was purchased by a European squillionaires, made by Swiss watchmaker Vacheron Constantin, making it the most expensive in the world's new hour. This clock takes years to make. Following features:
* Perpetual calendar and leap year
* Star chart and celestial annual calendar
* Tourbillon regulator
* Sunrise and sunset indication,
* Perpetual-time equation
* Phases and age of the moon
* Substantial power reserve
* Multiple time zones and day-night indication,
10. Rare photos of Marilyn Monroe Worth U.S. $ 150,000 dollars (1.5 Billion)
Watches costing U.S. $ 6.5 million dollars (65 billion) was purchased by a European squillionaires, made by Swiss watchmaker Vacheron Constantin, making it the most expensive in the world's new hour. This clock takes years to make. Following features:
* Perpetual calendar and leap year
* Star chart and celestial annual calendar
* Tourbillon regulator
* Sunrise and sunset indication,
* Perpetual-time equation
* Phases and age of the moon
* Substantial power reserve
* Multiple time zones and day-night indication,
10. Rare photos of Marilyn Monroe Worth U.S. $ 150,000 dollars (1.5 Billion)
 Collection of 36 rare photographs of this is estimated to last pictures of Marilyn Monroe star who sold last year for U.S. $ 150,000 dollars (1.5 billion) at auction in New York. This legendary actress posing naked in this photo for Vogue magazine in 1962, just six weeks before his death due to overdose. These photographs were taken by photographer Bert Stern, who eventually published in the magazine and became the last memories of this legendary actress.
Collection of 36 rare photographs of this is estimated to last pictures of Marilyn Monroe star who sold last year for U.S. $ 150,000 dollars (1.5 billion) at auction in New York. This legendary actress posing naked in this photo for Vogue magazine in 1962, just six weeks before his death due to overdose. These photographs were taken by photographer Bert Stern, who eventually published in the magazine and became the last memories of this legendary actress.
More Database Lesson.Candidate Key.
 here we go.....
Candidate key
In the relational model, a candidate key of a relvar (relation variable) is a set of attributes of that relvar such that
* (1) at all times it holds in the relation assigned to that variable that there are no two distinct tuples with the same values for these attributes and
* (2) there is not a proper subset for which (1) holds.
Since a superkey is defined as a set of attributes for which (1) holds we can also define candidate keys as minimal superkeys, i.e., superkeys of which no proper subset is also a superkey.
The importance of candidate keys is that they tell us how we can identify individual tuples in a relation. As such they are one of the most important types of database constraint that should be specified when designing a database schema. Since a relation is a setInsertformulahere, it holds that every relation will have at least one candidate key (because the entire heading is always a superkey). Since in some RDBMSs tables may also represent multisets (which strictly means these DBMSs are not relational), it is an important design rule to specify explicitly at least one candidate key for each relation. For practical reasons RDBMSs usually require that for each relation one of its candidate keys is declared as the primary key, which means that it is considered as the preferred way to identify individual tuples. Foreign keys, for example, are usually required to reference such a primary key and not any of the other candidate keys.
In other words, a candidate key is a field or combination of fields that can act as a primary key field for that table to uniquely identify each record in that table.
The definition of candidate keys can be illustrated with the following (abstract) example. Consider a relation variable (relvar) R with attributes (A, B, C, D) that has only the following two legal values r1 and r2:
r1 A B C D
a1 b1 c1 d1
a1 b2 c2 d1
a2 b1 c2 d1
r2 A B C D
a1 b1 c1 d1
a1 b2 c2 d1
a1 b1 c2 d2
Here r2 differs from r1 only in the A and D values of the last tuple.
For r1 the following sets have the uniqueness property, i.e., there are no two tuples in the instance with the same values for the attributes in the set:
{A,B}, {A,C}, {B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
For r2 the uniqueness property holds for the following sets;
{B,D}, {C,D}, {B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
Since superkeys of a relvar are those sets of attributes that have the uniqueness property for all legal values of that relvar and because we assume that r1 and r2 are all the legal values that R can take, we can determine the set of superkeys of R by taking the intersection of the two lists:
{B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
Finally we need to select those sets for which there is no proper subset in the list, which are in this case:
{B,C}, {A,B,D}, {A,C,D}
These are indeed the candidate keys of relvar R.
We have to consider all the relations that might be assigned to a relvar to determine whether a certain set of attributes is a candidate key. For example, if we had considered only r1 then we would have concluded that {A,B} is a candidate key, which is incorrect. However, we might be able to conclude from such a relation that a certain set is not a candidate key, because that set does not have the uniqueness property (example {A,D} for r1). Note that the existence of a proper subset of a set that has the uniqueness property cannot in general be used as evidence that the superset is not a candidate key. In particular, note that in the case of an empty relation, every subset of the heading has the uniqueness property, including the empty set.
The previous example only illustrates the definition of candidate key and not how these are in practice determined.. Since most relations have a large number or even infinitely many instances it would be impossible to determine all the sets of attributes with the uniqueness property for each instance. Instead it is easier to consider the sets of real-world entities that are represented by the relation and determine which attributes of the entities uniquely identify them. For example a relation Employee(Name, Address, Dept) probably represents employees and these are likely to be uniquely identified by a combination of Name and Address which is therefore a superkey, and unless the same holds for only Name or only Address, then this combination is also a candidate key.
In order to determine correctly the candidate keys it is important to determine all superkeys, which is especially difficult if the relation represents a set of relationships rather than a set of entities. Therefore it is often useful to attempt to find any "forgotten" superkeys by also determining the functional dependencies. Consider for example the relation Marriage(Man, Wife, Date) for which it will trivially hold that {Man, Wife, Date} is a superkey. If we assume that a certain person can only marry once on a given date then this implies the functional dependencies {Man,Date}→Wife and {Wife,Date}→Man. From this then we can derive more superkeys by applying the following rule:
if S is a superkey and X→Y a functional dependency
then (S-Y)+X is also a superkey
where '-' is the set difference and '+' the set union. In this case this leads to the derivation of the superkeys {Man, Date} and {Wife, Date}.
here we go.....
Candidate key
In the relational model, a candidate key of a relvar (relation variable) is a set of attributes of that relvar such that
* (1) at all times it holds in the relation assigned to that variable that there are no two distinct tuples with the same values for these attributes and
* (2) there is not a proper subset for which (1) holds.
Since a superkey is defined as a set of attributes for which (1) holds we can also define candidate keys as minimal superkeys, i.e., superkeys of which no proper subset is also a superkey.
The importance of candidate keys is that they tell us how we can identify individual tuples in a relation. As such they are one of the most important types of database constraint that should be specified when designing a database schema. Since a relation is a setInsertformulahere, it holds that every relation will have at least one candidate key (because the entire heading is always a superkey). Since in some RDBMSs tables may also represent multisets (which strictly means these DBMSs are not relational), it is an important design rule to specify explicitly at least one candidate key for each relation. For practical reasons RDBMSs usually require that for each relation one of its candidate keys is declared as the primary key, which means that it is considered as the preferred way to identify individual tuples. Foreign keys, for example, are usually required to reference such a primary key and not any of the other candidate keys.
In other words, a candidate key is a field or combination of fields that can act as a primary key field for that table to uniquely identify each record in that table.
The definition of candidate keys can be illustrated with the following (abstract) example. Consider a relation variable (relvar) R with attributes (A, B, C, D) that has only the following two legal values r1 and r2:
r1 A B C D
a1 b1 c1 d1
a1 b2 c2 d1
a2 b1 c2 d1
r2 A B C D
a1 b1 c1 d1
a1 b2 c2 d1
a1 b1 c2 d2
Here r2 differs from r1 only in the A and D values of the last tuple.
For r1 the following sets have the uniqueness property, i.e., there are no two tuples in the instance with the same values for the attributes in the set:
{A,B}, {A,C}, {B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
For r2 the uniqueness property holds for the following sets;
{B,D}, {C,D}, {B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
Since superkeys of a relvar are those sets of attributes that have the uniqueness property for all legal values of that relvar and because we assume that r1 and r2 are all the legal values that R can take, we can determine the set of superkeys of R by taking the intersection of the two lists:
{B,C}, {A,B,C}, {A,B,D}, {A,C,D}, {B,C,D}, {A,B,C,D}
Finally we need to select those sets for which there is no proper subset in the list, which are in this case:
{B,C}, {A,B,D}, {A,C,D}
These are indeed the candidate keys of relvar R.
We have to consider all the relations that might be assigned to a relvar to determine whether a certain set of attributes is a candidate key. For example, if we had considered only r1 then we would have concluded that {A,B} is a candidate key, which is incorrect. However, we might be able to conclude from such a relation that a certain set is not a candidate key, because that set does not have the uniqueness property (example {A,D} for r1). Note that the existence of a proper subset of a set that has the uniqueness property cannot in general be used as evidence that the superset is not a candidate key. In particular, note that in the case of an empty relation, every subset of the heading has the uniqueness property, including the empty set.
The previous example only illustrates the definition of candidate key and not how these are in practice determined.. Since most relations have a large number or even infinitely many instances it would be impossible to determine all the sets of attributes with the uniqueness property for each instance. Instead it is easier to consider the sets of real-world entities that are represented by the relation and determine which attributes of the entities uniquely identify them. For example a relation Employee(Name, Address, Dept) probably represents employees and these are likely to be uniquely identified by a combination of Name and Address which is therefore a superkey, and unless the same holds for only Name or only Address, then this combination is also a candidate key.
In order to determine correctly the candidate keys it is important to determine all superkeys, which is especially difficult if the relation represents a set of relationships rather than a set of entities. Therefore it is often useful to attempt to find any "forgotten" superkeys by also determining the functional dependencies. Consider for example the relation Marriage(Man, Wife, Date) for which it will trivially hold that {Man, Wife, Date} is a superkey. If we assume that a certain person can only marry once on a given date then this implies the functional dependencies {Man,Date}→Wife and {Wife,Date}→Man. From this then we can derive more superkeys by applying the following rule:
if S is a superkey and X→Y a functional dependency
then (S-Y)+X is also a superkey
where '-' is the set difference and '+' the set union. In this case this leads to the derivation of the superkeys {Man, Date} and {Wife, Date}.
Database? hmm...got it here...
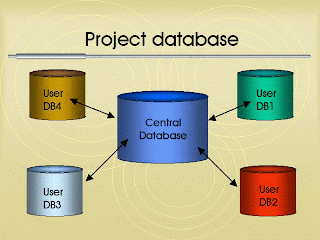 Collection of data items that are interconnected with each other which are organized according to a scheme or a particular structure, stored in the computer hardware and software to perform manipulation for certain uses which defines There is also a database is a collection of information stored in the computer in a systematic way so that can be checked using a computer program to obtain information from these databases
Need reasons Database
· Database is one important component in the system information, because it is fundamental in providing information.
· Database determines the quality of information: accurate, timely and relevant. Information can be said is worth more effective if its benefits compared to cost to get it.
· Database reduces duplication of data (data redudancy).
• By applying database data relationships can be improved.
· Database can reduce waste places outside savings.
Database language
Data base consisting of Language
Data Definition Language (DDL), refers to a collection of commands that can be used to define the object - the object database, such as creating a database table or an index of primary or secondary.
Data Manipulation Language (DML is), refers to a collection of commands that can be used to perform data manipulation, such as storing data into a table, then change it and delete it or just display it again.
Objective Data Base
More fully, the utilization of the database is to fulfill some purpose (objective) as follows
a. Speed and convenience (Speed)
b. The efficiency of storage space (Space)
c. Accuracy (Accuracy)
d. Availability (Avaibility)
e. Completeness (Completeness)
f. Security (Security)
g. Togetherness usage (Sharability)
SQL (Structured Query Language)
SQL is the language used to communicate with the database. According to ANSI (American National Standards Institute), this is a standard language for relational database management systems (RDBMS)
SQL statements used to perform several tasks such as update data in a database or displaying data from the database. Almost all SQL database software to implement the language as a major component of its product, one of MySQL.
MySQL
To make the administration of MySQL database, can use the module that is included is a command-line (commands: mysql and mysqladmin). Can also be downloaded from the MySQL site that is a module of the graphical (GUI): MySQL Administrator and MySQL Query Browser. In addition there is also a free software for administration of web-based MySQL database that is very popular phpMyAdmin. For software for MySQL database administration sold commercially, among others: the MySQL front, Navicat and EMS SQL Manager for MySQL
MySQL Basic Commands
SQL language has a structure that is easy to understand because the command - the command is basically made from English. So that we can do a command - SQL command into the MySQL database, ie
a. Inserting or adding new records to the database.
b. Execute database queries
c. Taking data from database
d. Changing records in the database
e. Deleting records in the database
SQL commands can be typed in capital letters or small (non case sensitive). When you finish typing the command in MySQL should end with a semicolon as a marker of the end of the MySQL command. SQL commands can be typed in capital letters or small (non case sensitive). When you finish typing the command in MySQL should end with a semicolon as a marker of the end of the MySQL command.
Collection of data items that are interconnected with each other which are organized according to a scheme or a particular structure, stored in the computer hardware and software to perform manipulation for certain uses which defines There is also a database is a collection of information stored in the computer in a systematic way so that can be checked using a computer program to obtain information from these databases
Need reasons Database
· Database is one important component in the system information, because it is fundamental in providing information.
· Database determines the quality of information: accurate, timely and relevant. Information can be said is worth more effective if its benefits compared to cost to get it.
· Database reduces duplication of data (data redudancy).
• By applying database data relationships can be improved.
· Database can reduce waste places outside savings.
Database language
Data base consisting of Language
Data Definition Language (DDL), refers to a collection of commands that can be used to define the object - the object database, such as creating a database table or an index of primary or secondary.
Data Manipulation Language (DML is), refers to a collection of commands that can be used to perform data manipulation, such as storing data into a table, then change it and delete it or just display it again.
Objective Data Base
More fully, the utilization of the database is to fulfill some purpose (objective) as follows
a. Speed and convenience (Speed)
b. The efficiency of storage space (Space)
c. Accuracy (Accuracy)
d. Availability (Avaibility)
e. Completeness (Completeness)
f. Security (Security)
g. Togetherness usage (Sharability)
SQL (Structured Query Language)
SQL is the language used to communicate with the database. According to ANSI (American National Standards Institute), this is a standard language for relational database management systems (RDBMS)
SQL statements used to perform several tasks such as update data in a database or displaying data from the database. Almost all SQL database software to implement the language as a major component of its product, one of MySQL.
MySQL
To make the administration of MySQL database, can use the module that is included is a command-line (commands: mysql and mysqladmin). Can also be downloaded from the MySQL site that is a module of the graphical (GUI): MySQL Administrator and MySQL Query Browser. In addition there is also a free software for administration of web-based MySQL database that is very popular phpMyAdmin. For software for MySQL database administration sold commercially, among others: the MySQL front, Navicat and EMS SQL Manager for MySQL
MySQL Basic Commands
SQL language has a structure that is easy to understand because the command - the command is basically made from English. So that we can do a command - SQL command into the MySQL database, ie
a. Inserting or adding new records to the database.
b. Execute database queries
c. Taking data from database
d. Changing records in the database
e. Deleting records in the database
SQL commands can be typed in capital letters or small (non case sensitive). When you finish typing the command in MySQL should end with a semicolon as a marker of the end of the MySQL command. SQL commands can be typed in capital letters or small (non case sensitive). When you finish typing the command in MySQL should end with a semicolon as a marker of the end of the MySQL command.
The Secret behind Compact Disc
 I'd want to make a posting about the notion of hardware, but in because I have received a good lesson, so I am not so to post about the hardware, but instead I'll reveal the secret behind a compact disc. I'm sure there are many who do not know about this CD. either that, in making or history or the other, well now is the time for me to unlock all the secrets behind this CD.
enjoy it.
CD media is no longer strange stuff. Many people who often play with the pieces of CD for various purposes. There is a photograph in the studio and the photos stored on CD, some songs make the album and the results are stored on the CD, there is also a film and the results are also stored in the CD fragment.
CD-ROM stands for Compact Disc - Read Only Memory. CD-ROM disc is colored silver. The drafting process is a way to put a sheet of plastic film that has been illuminated by a laser beam. The laser beam will form a pit (hole) are microscopic, which is very small. The holes that will form the contents of the code sequence data. Once a hole is created, it can not be closed again. Then it will be wrapped in a plastic layer again by liquid plastic that is useful as a protector and reflectors. All that the process is done gradually in a molding machine. CD-ROM tool mold shaped like a cookie cutter and the analogy of making sweet pancake also similar. More details download the full text.
I'd want to make a posting about the notion of hardware, but in because I have received a good lesson, so I am not so to post about the hardware, but instead I'll reveal the secret behind a compact disc. I'm sure there are many who do not know about this CD. either that, in making or history or the other, well now is the time for me to unlock all the secrets behind this CD.
enjoy it.
CD media is no longer strange stuff. Many people who often play with the pieces of CD for various purposes. There is a photograph in the studio and the photos stored on CD, some songs make the album and the results are stored on the CD, there is also a film and the results are also stored in the CD fragment.
CD-ROM stands for Compact Disc - Read Only Memory. CD-ROM disc is colored silver. The drafting process is a way to put a sheet of plastic film that has been illuminated by a laser beam. The laser beam will form a pit (hole) are microscopic, which is very small. The holes that will form the contents of the code sequence data. Once a hole is created, it can not be closed again. Then it will be wrapped in a plastic layer again by liquid plastic that is useful as a protector and reflectors. All that the process is done gradually in a molding machine. CD-ROM tool mold shaped like a cookie cutter and the analogy of making sweet pancake also similar. More details download the full text.
History of Pentium.Did you Know?
We already know the word Pentium in the computer world for almost a decade. The name of the processor that Intel has become the spearhead in the desktop PC processor market share of this world is better known than the original meaning of the word Pentium are indeed in a sense the Greek means 5 (five) is, indeed Intel chose this name because of the Pentium processor was originally an Intel processor generations to five. Cute maybe if you think that the Pentium 4 processor latest 32-bit Intel, which still bears the name of the Pentium processor to their name indicates that this is still the fifth-generation processors. Yet if we look at changes in the architecture of Intel's latest processor, perhaps more accurately represents the seventh generation. Maybe it should Septium or something like that is, right? hehe ... Well even if that reason it seems less appropriate, another reason why Intel has the Pentium is still the primary name of Intel processor product line, because the Pentium name has become a brand-name processors, people only know the Pentium and Pentium only, perhaps feared that Intel uses strange names again, people will become confused. Hmm ... good reason too ... In this article I want to tell you the reader, Pentium history from the beginning to the last generation of Pentium. Hopefully this article can add insight to your computer and provides a description of the development of this processor in terms of its architecture.
The Story Begins here ... ..
Pentium Launched around early 90's, precisely 1993, the Pentium is a big leap in the history of the X86 processor where the processor 32-bit architecture experience tremendous change. This causes the speed of the Pentium (80586th or simply 586) in a clock-for-clock with the processor 486 (previous generation) is much faster. Starting with a speed of 60 MHz to 233 MHz, this processor has made a new revolution in the PC world. In the first version (Pentium 60 MHz) processor never makes a scene in the PC world because, according to a professor, the processor has done a calculation error when done combination of multiplication and rooting calculation. It is recognized by Intel that pulled back the entire 60 MHz Pentium processor at the same time remove the fleet 60 and 66 Mhz processor which then replaced with a Pentium 75 Mhz. In Indonesia, some in other countries, the authors observed that the Pentium processor is the most widely used is a Pentium 133 Mhz processor, your readers may never have them? Intel makes the Pentium chipset is starting from FX, HX, VX until that is able to support the final version of the Pentium with MMX, TX chipset, the form of packaging is a Socket-7 processors. Pentium architecture of a slight change in line with developments in technology with the introduction of new multimedia instructions, called MMX in 1994. Although its told by Intel processor with this capability that can enhance the multimedia experience (a multimedia experience) up to 30-50%, but in reality this instruction set is not used by many multimedia programmers (especially games). But these MMX instructions is the origin of SIMD instructions (Single Instruction Multiple Data), which has since been developed. Instructions 3DNow! Of AMD as an example is an improved version of the MMX instructions, so too ISSE (Internet Streaming SIMD Extension) Intel's own. Pentium Pro During development, Intel also makes the Pentium made specifically for high performance computers, such as servers, namely the Pentium Pro. For the first time brings together Intel's L2 cache into the processor. Not many outstanding Pentium Pro, was due to the extremely high cost of a processor, even until today! It is not surprising that only a few speed grades available for the Pentium Pro, between 200 MHz s / d 233 Mhz. If you are casually looking for this type of processor, you will be amazed at the price, especially when compared with the elements of the technology. Yet the basic architecture of the Pentium Pro is the foundation of the development of Pentium II. The weakness of the Pentium Pro is weak ability to run 16-bit long program, this is due to the early architecture of this processor is preferred for 32-bit applications. It is no wonder that the Pentium Pro's performance under or equivalent to Pentium when running the application 16 & 32-bit like Windows9X. Another story if you use this processor in Windows NT that design is completely original 32-bit. Pentium II With the development codenamed 'Klamath', Pentium II represents a significant improvement from the old Pentium architecture. Changes in the structure and a large cache, L2-cache placements, as well as a striking way of packaging the new processor, PPGA (Plastic Pin Grid Array), which Intel once thought to reduce production cost of the processor. Changes in the form of packing these processors make motherboards makers were forced to change the processor from the socket to house slots, called Slot-1. In this way, the processor is plugged into an available slot, similar to a stuck expansion card. Intel chipsets early (and still is the best chipset so far) for Pentium II is i440BX for standard PCs, as well as i440LX for budget PCs. Placement within the processor L2 cache but not in the middle is also a major difference with a Pentium PII. If the cache was placed on the motherboard, this time to put Intel processors cache on circuit boards. This can improve processor performance because cache work at ½ the processor's clock, so if the processor works at 350 Mhz, cache means working at 175 Mhz. This is a significant improvement from the old architecture cache working on a particular clock is set motherboard. On Pentium II also improved the performance of 16-bit from its predecessor, the Pentium Pro. So in running application mix 16 & 32-bit speed can be fueled. Large core Pentium II also smaller, this is because the processor was made at 0:25-micron processing. Speed levels starting from Pentium II 233 Mhz PII to PII 450 Mhz. Where the level of speed is most often found between 300-450 Mhz. Celeron Intel saw a large enough market in the precious PCs under $ 1,000, where performance is not too concerned, roughly computer 'is an important way'. Intel to enter this market by launching a Celeron processor, a variant of the Pentium II with '39; some ability PII, at the end of 1998. the Celeron can be seen from the absence of L2 cache and FSB limitation that if PII can be up to 100 Mhz, 66 Mhz Celeron only. Both restrictions can reduce the price to almost ½ PII Celeron, of course with a performance penalty is bad enough. Celeron is a poor performance had been criticized by computer enthusiasts, especially because of the absence of L2 cache which is very influential on processor performance. Therefore, Intel launched the added L2 cache Celeron but only 128 KB, the chace is less than 512 KB PII, 300 MHz at the levels of speed, so the market there are 2 kinds Celeron 300 Mhz, which is the L2 cache and with no L2 cache. The difference can be seen from the initials of A behind the rate of speed, so that the L2 cache Celeron be named Celeron 300A. Since then, all above 300 Mhz Celeron will have 128 KB L2 cache. But all of them do not make better than a PIII Celeron until the final version too, that besides her due to the FSB 66Mhz only, its L2 cache is also the only 4-way set associative, unlike the 8-way PIII set associative, And that matters much! Looks like a castrated processors really well? Due to the absence or at least L2 cache, Celeron processors that are most easily seen in the overclock. L2 cache affects the ability to overclock the processor because it increased the frequency of the processor beyond its ability of the clock then automatically on the cache's clock is also raised. If you do not have the cache then the problem is even easier. The author never heard if there is capable of overclocked Celeron with an increase up to 400-450 MHz, so if there is a Celeron 300 Mhz in overclock, it could increase up to 700-750 Mhz! Benerrr gile ... ... FSB is also a bottleneck that prevents the Celeron to compete with her brothers. With 66 Mhz FSB, a new Celeron processor may compete with PII, if the speed is faster ¾ it, and it was quite disturbing too, I think this is a strategy to avoid Intel Celeron to compete directly with other fleet fast processor on Intel's own. One thing to note, the Celeron is Intel's first processors that use Socket 370, so the form back to the processor as it used to anymore, and have a square foot a lot (in this case 370 pin) underneath. This continued on until now, may mark the beginning of death Slot-1 Celeron Socket ... Laying the core of this new model too, called FC-PGA (Flip-Chip Pin Grid Array) processor core which is placed on the top surface of the processor, so it can remove more heat good. The final version of the Celeron, Celeron II, contains the architecture better than his brother, because its architecture, based on the PIII and already has ISSE once only owned by PIII. As well as having forms are not slot back into the socket again, but like the old Pentium. And also the Celeron II has been produced in 0:18-micron. But in the near future Intel reportedly plans to create a Celeron II with 100MHz FSB, and it is good news. Pentium III (Merced) With the development codenamed Merced, Pentium III are made for improving the existing weaknesses in the Pentium II and by personal author is also an answer to Intel from a K6-2 AMD processors that have special instructions 3DNow!, Since the PII has no special instructions such , except for Intel's MMX own. In PIII processor which is still produced in 0:25-micron, has done a fairly fundamental change. Things changed in the presence of PIII is ISSE instructions on Intel's MMX is an extension of itself. These processors L2 cache which is still outside the core processor, although at this stage, Intel has started to realize that this cache architecture does not help the performance of the processor and its technology has been able to unite, in order to maintain compatibility in the slot, Intel was forced to make this processor is still in the form of slots. Pentium III (Coppermine) Launched in early 2000, the 2nd generation processors from this PIII PIII fix almost any deficiencies early generations, all are also introduced for the first time the latest technology, Intel FC-PGA in the manufacture of the processor and of course has been processed at the 0:18-micron. 133 Mhz FSB also introduced so that it can boost processor performance. Although most processors on Socket shape again, but for some speed Grades still retain the shape of his Slot-1 motherboard, motherboard compatibility for long. Pentium III model has many possible models to be confusing. Especially those with 600MHz speed grades and above, for example at 600 MHz speed grade there are 600, 600E, 600EB, there is also a 600B. E shows that the initials FSB 600MHz PIII 133 Mhz that was, if his initials B shows that the shape is FC-PGA (Socket 370 PIII-shaped). Quite confusing is not for just one processor model? But for those above 800 Mhz, most or perhaps all processors must have a 133 Mhz FSB bus and been shaped Socket FC-PGA PIII generari latest development of this second is from the new management system cachenya, called ATC or Advanced Transfer Cache, which allows the cache that can be installed on this PIII data oversee what is most often used on the activities of certain processes. Also added approximately 20 30s new multimedia instructions that by Intel called ISSE II. Coppemine managed to penetrate the boundary PIII 1 Ghz Ghz in the race who have 'held' around the second quarter of this year. Although beaten by AMD which has reached the first 1 GHz, Intel seems to have a lot to make changes here and there so that the processor can be 'forced' to achieve 1 GHz. Highest PIII processor time of writing this article has reached 1:13 GHz. Pentium III (Tualatin) Pentium III-3 generation was rumored to be launched in the quarter to 1 or 2 years old in 2001, in addition will have a higher clock will also be made on Intel's newest processing, 0:13-micron. One thing that is interesting from Tualatin PIII processor supports the use of 200 MHz bus, although still maintaining the form of its Socket-370. Obviously this will not make the old motherboard can support PIII Tualatin. Intel reportedly will not directly use the capabilities of this new PIII 200 Mhz to avoid direct competition with his brother, the Pentium 4. New PIII It will also support both SDRAM and DDR SDRAM. Pentium 4 (Willamette) Latest from the Pentium processor family is Pentium 4 (P4), the project has begun Intel since 1-2 years ago. With the 1.4 GHz speed grades as the smallest to make the P4 to P4 is 32-bit processor was the fastest time. Created in 0:18-micron processing for initial versions, P4 will gradually move to the 0:13-micron along with the increase the clock. It is estimated that Q4 will be able to be made up to 2 GHz range. By using the new chipset coded 'Tehama', this processor will plans on to use Rambus memory as its interface, this is because this is more optimalized processor architecture on the architecture of Rambus. Rambus as the memory usage to make the expensive of a system that uses this P4, a large piece of 64MB RIMM, the price could reach $ 400's, try as compared with ordinary SDRAM DIMMs that cost just $ 70's, the difference was not? But if you look at performance obtained, it seems likely that expensive price is not reasonable? These architectural changes also make the P4 core size becomes larger, an approximately 200-mm2, compared with the PIII core of just 150 mm2. This makes the P4 processor requires a larger heatsink and cooling frame is stronger too. Not to mention because of the 'new' chassis this makes the designers must create a new model chassis that can house the P4, this standard has been prepared under the name Intel ATX 2.0. So who hopes to be able to upgrade it to a P4 PIII can you throw it, quite unfortunate at all! But that's the risk of technological developments. This suggests that P4 is a fairly expensive investment, it is no wonder if the P4 for a while is intended only for the server only, not for the desktop, but there is also a plan towards it. About P4 details can be found on the news along with the opening of information on the P4. Pentium V (?) So far this is still a rumor that Intel would develop a Pentium V, V is probably the last generation of Pentium and Pentium processors as well as the latest generation 32-bit Intel. Not much info to get this far. So my article on the history and development of the Intel Pentium and variant-variant, hopefully this information can increase your knowledge about computers, especially in the field of processors.
and know what do you think about this history??
Kind of Network
- Network science
- Network (mathematics), a type of digraph in graph theory
- Network theory, an area of applied mathematics and part of graph theory
- Network analysis (electrical circuits)
- Network diagram, a diagram of a network
- Network model, a database model
- Network (film), a 1976 Oscar-winning movie
- NETWORK (lobbying group), an American social justice group
- The Network, an American New Wave band
- Network DVD, a British publisher
- Network (comics), a series of Marvel characters
Hello World
 Hello world. ^_^
this is my blog.I will fill this blog with my lesson in college, and because I study at informatics college, so that my blog's title is Informatics Management.I want to share my knowledge at university to everybody entire this world.
Hello world. ^_^
this is my blog.I will fill this blog with my lesson in college, and because I study at informatics college, so that my blog's title is Informatics Management.I want to share my knowledge at university to everybody entire this world.





